This guide will show how to configure Dataedo to work with a SAML identity provider. For this article, we'll be using Google Workspace as the IdP, but similar steps can be taken for other providers too.
Initial configuration in Google Admin Portal (SAML provider)
Open Google Admin Portal and go to Apps and then Web and mobile apps, click on Add app and select Add custom SAML app.
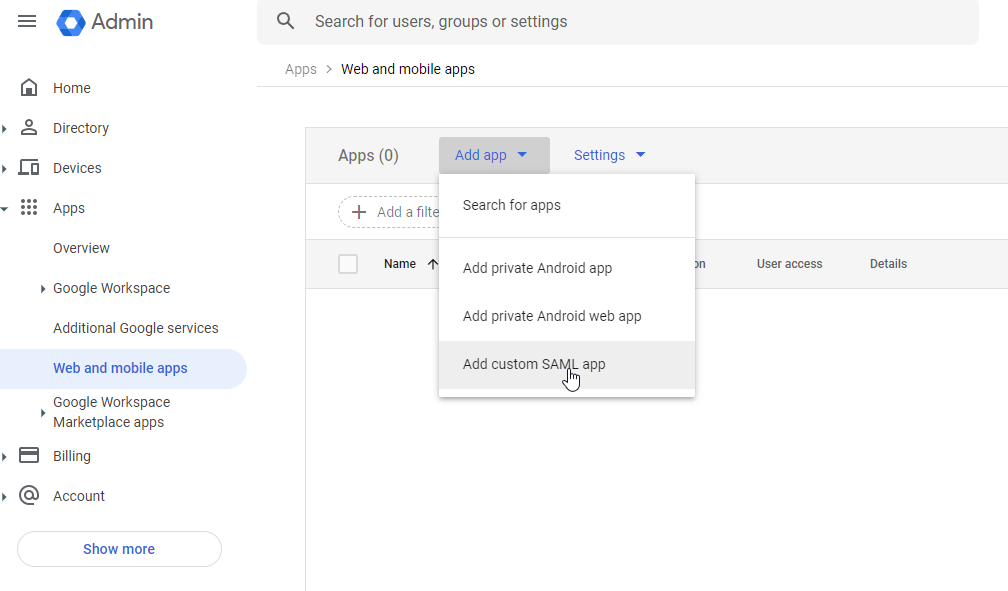
In the newly opened tab type in the application name for your internal use (I chose "Dataedo Portal") and click Continue.

On the next page click DOWNLOAD METADATA to download the metadata file, we will need it later, after that click Continue.

On this page under ACS URL field type in the address your Dataedo Portal will be accessed on followed by /api/api/auth/assertion-consumer (for example https://your-Dataedo-Web.address/api/api/auth/assertion-consumer), for Entity ID it's up to you how you will call it, don't use spaces nor special characters and save it for later use.
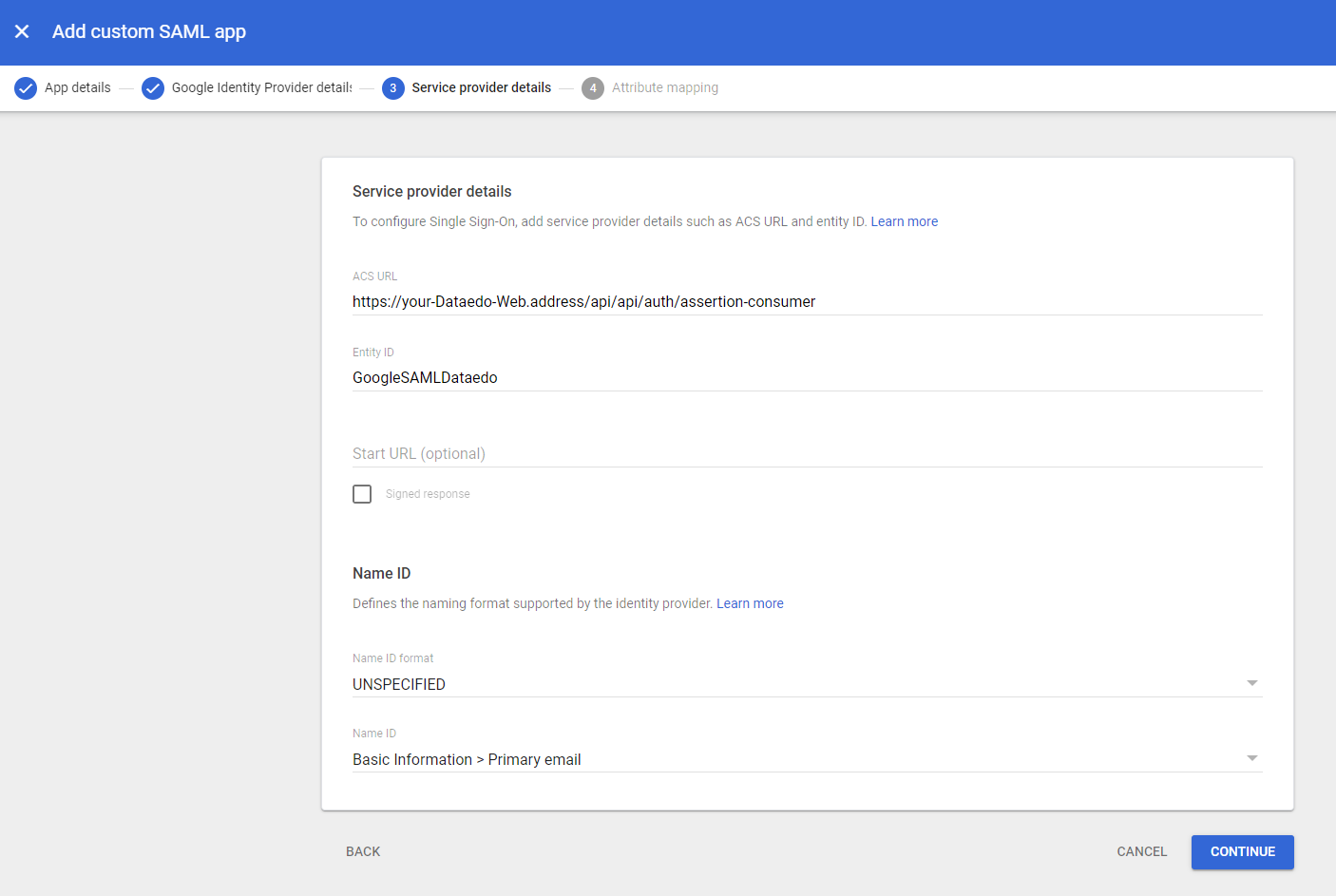
On the last page none of the fileds are required so you can just click Finish.
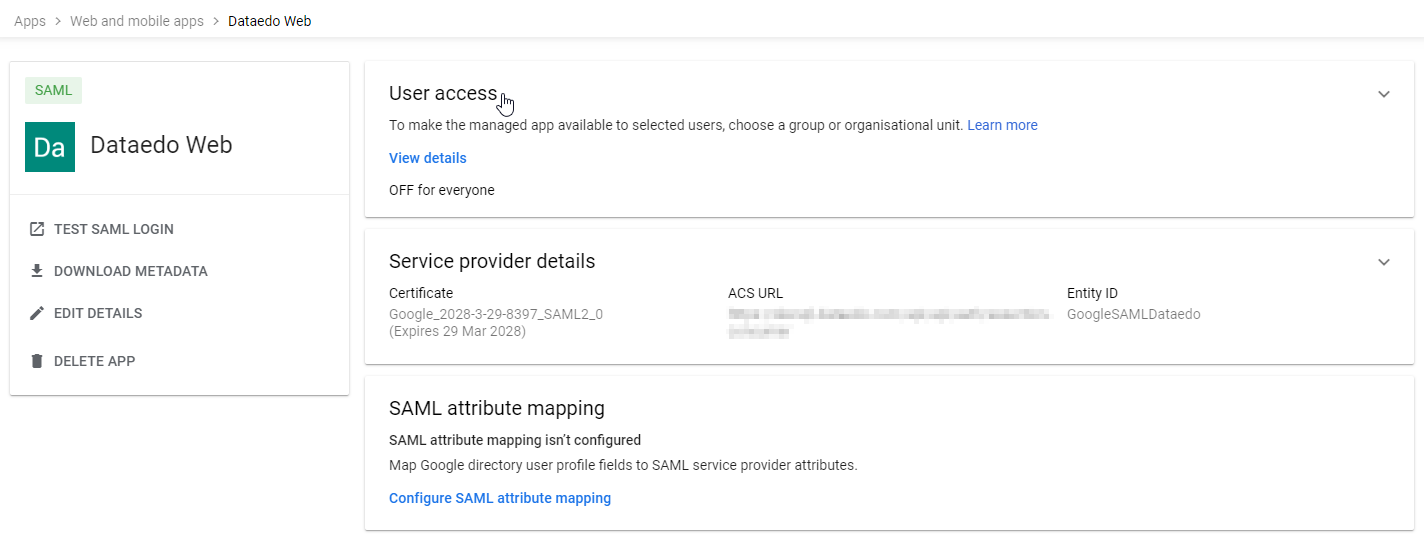
On the app page click on User access and assign user/group that should be allowed to login to Dataedo Web using Google SAML.
Configuring SAML in Dataedo Web settings file
Follow this section for Dataedo installed on a Windows machine.
Find the installation path of Dataedo Web (default address is: *C:\Dataedo Web*), then go to Applications\API\ subfolder.
Right click and edit the appsettings.json file, and find the Saml2 section:
"Saml2": {
"IdPMetadata": "",
"Issuer": "",
"SignatureAlgorithm": "http://www.w3.org/2001/04/xmldsig-more#rsa-sha256",
"CertificateValidationMode": "ChainTrust",
"RevocationMode": "NoCheck"
},
In the IdPMetadata field paste in the path for the metadata xml file that you saved on your machine in previous step. Please use below format: {drive letter}:/Path/to/file/GoogleIDPMetadata.xml. For example: C:/Dataedo Web/GoogleIDPMetadata.xml
In the Issuer field, paste the Entity ID field from Google Admin Portal that you configured earlier (you can check it in Service provider details > Entity ID field in the application details in Google Portal).
If required, correct the signature algorithm if you don’t use the default RSA_SHA256 algorithm - for example, for RSA_SHA1 the field should have the http://www.w3.org/2001/04/xmldsig-more#rsa-sha1 value.
Find the Saml2Client section:
"Saml2Client": {
"DisplayName": "",
"ClientUrl": "http://192.168.0.21:80"
},
Fill the DisplayName field – this will be the name shown when logging in to Dataedo for the Identity Provider.
Make sure the ClientUrl field correctly leads to your Dataedo Web address.
After changes, the edited parts should look like this:
"Saml2": {
"IdPMetadata": "C:/Dataedo Web/GoogleIDPMetadata.xml",
"Issuer": "GoogleSAMLDataedo",
"SignatureAlgorithm": "http://www.w3.org/2001/04/xmldsig-more#rsa-sha256",
"CertificateValidationMode": "ChainTrust",
"RevocationMode": "NoCheck"
},
"Saml2Client": {
"DisplayName": "Google SAML",
"ClientUrl": "https://127.0.0.1:4435"
},
Go to IIS Manager, and restart the Dataedo Web app for changes to take effect.
The next time you open Dataedo Web, you should have an option to login with Google:
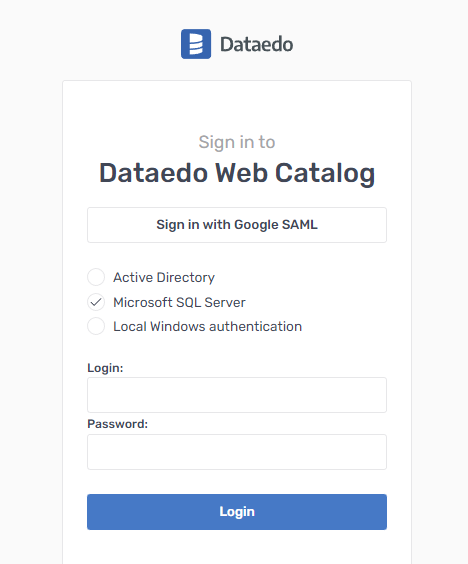
Clicking it will either take you to the Google login page or if you’re already logged in, directly to your Dataedo Web page.
Configuring SAML in Dataedo Web Docker image
Follow this section for Web Catalog running from a Docker image.
Open .env file that should be located in same folder as docker-compose.yml file, find Single Sign On section:
#Single Sign On
DATAEDO_SSO_IDP_METADATA=
DATAEDO_SSO_ISSUER=
DATAEDO_SSO_SIGNATURE_ALGORITHM=http://www.w3.org/2001/04/xmldsig-more#rsa-sha256
DATAEDO_SSO_CERTIFICATE_VALIDATION_MODE=ChainTrust
DATAEDO_SSO_REVOCATION_MODE=NoCheck
DATAEDO_SSO_DISPLAY_NAME=
DATAEDO_SSO_CLIENT_URL=
In the DATAEDO_SSO_IDP_METADATA field paste in the path for the metadata xml file that you saved on your machine in previous step.
In the DATAEDO_SSO_ISSUER field, paste the Entity ID field from Google Admin Portal that you configured earlier (you can check it in Service provider details > Entity ID field in the application details in Google Portal).
If required, correct the signature algorithm if you don’t use the default RSA_SHA256 algorithm - for example, for RSA_SHA1 the field should have the http://www.w3.org/2001/04/xmldsig-more#rsa-sha1 value.
Fill the DATAEDO_SSO_DISPLAY_NAME field – this will be the name shown when logging in to Dataedo for the Identity Provider. The DisplayName value cannot contain blank spaces (you can use underscore _ instead).
Make sure the DATAEDO_SSO_CLIENT_UR field correctly leads to your Dataedo Web address.
After changes, the edited parts should look like this:
#Single Sign On
DATAEDO_SSO_IDP_METADATA="/opt/dataedo/idpmetadata/GoogleIDPMetadata.xml"
DATAEDO_SSO_ISSUER="GoogleSAMLDataedo"
DATAEDO_SSO_SIGNATURE_ALGORITHM=http://www.w3.org/2001/04/xmldsig-more#rsa-sha256
DATAEDO_SSO_CERTIFICATE_VALIDATION_MODE=ChainTrust
DATAEDO_SSO_REVOCATION_MODE=NoCheck
DATAEDO_SSO_DISPLAY_NAME="GoogleSAML"
DATAEDO_SSO_CLIENT_URL="https://yourwebiste.com/"
Update your Docker Compose with:
docker-compose up -d
The next time you open Dataedo Web, you should have an option to login with Google:

Clicking it will either take you to the Google login page or if you’re already logged in, directly to your Dataedo Web page.











 Marcin Gaweł
Marcin Gaweł